Overview
The system administrator can configure the system password management and storage options to find the correct balance between convenience, performance and security. The password and login options can be configured at the global level and at a per user level.
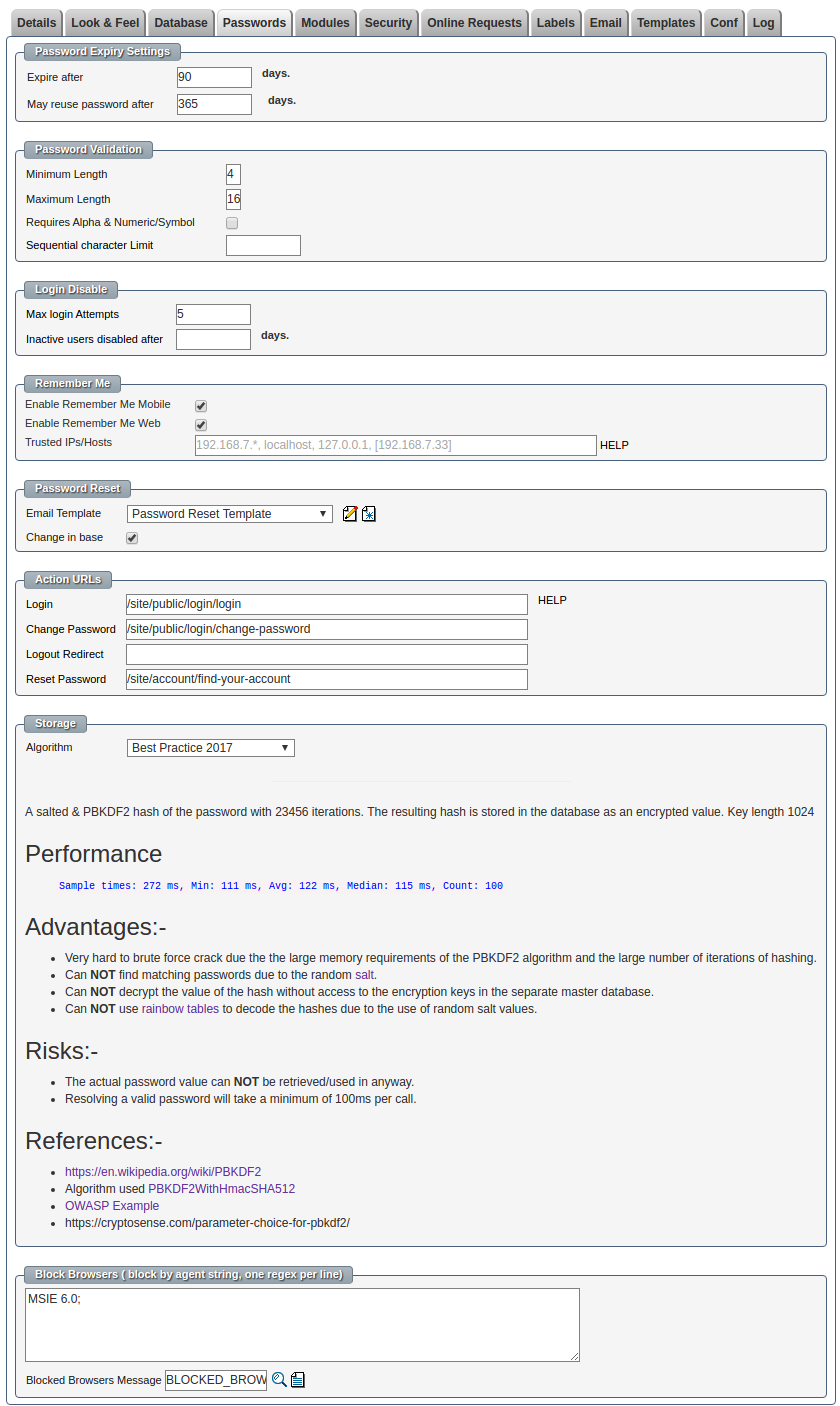
System Password Options
- Password expires after X days.
- The user will be required to enter a new password after this period has expired.
- Passwords can not be re-used within X days
- The minimum period before the user may re-use their old passwords.
- Passwords must have minimum length
- The longer the password, in general the harder the password is to guess.
- Passwords must have maximum length
- There is no practical system level length restriction.
- Passwords must include both alpha & numeric characters
- Requiring the user to create passwords with both alphabetic characters and numbers can increase the strength of the password.
- Passwords may not contain more than a set number of sequential characters.
- This option prevents the users from entering a password like '123456'
- The number of log in attempts before the user is disabled.
- This option prevents brute force attempts at guessing a user's password.
- The number of days before an inactive user is disabled.
- This option automatically disabled inactive users which reduces the opportunity for hackers to find and use an old account.
- The option use be set to a reasonably high number of days so that people aren't lockout just by going on leave.
- If "remember me" is enabled for desktop browsers.
- Should we offer to remember the user's with a permanent cookie on a desktop computer ?
- This is a very convenient feature but leads to a security risk if the computer is stolen.
- If "remember me" is enabled for mobile browsers.
- Should we offer to remember the user's with a permanent cookie on a mobile/tablet ?
- This is a very convenient feature but leads to a security risk if the computer is stolen.
- Remember me can be configured for use only within trusted zones.
- This allows for users to choose "remember me" within an office environment but will not be given as an option in the airport terminal.
- Even if the remember me option had been previously been checked on for a device with a "trusted zone" if an attempt to re-login when the device is now in a non-trusted zone the previous remember me request will be ignored.
- The email template to send the user when resetting their password.
- This email template can be customized to give detail instructions on special procedures for resetting passwords.
- The Action URLs allow the next step to be configured once a user logs in/out, changes a password or resets their password.
- The default storage algorithm
- The system default password storage algorithm can be overridden on a per login record basis.
- When a user's password is changed the password will be saved according to the chosen storage algorithm.
- Different algorithms have different properties such as performance and resistance to being decrypted.
- Block login attempts by browser strings.
- The system does not support IE6 so any attempt to login with this browser will be blocked and a message is shown.
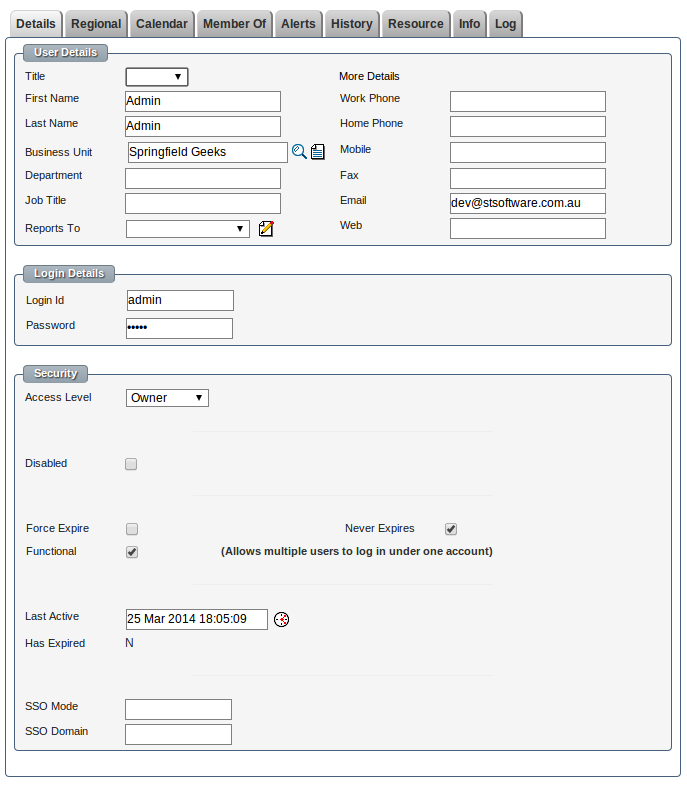
User Password Options
- General user contact details
- Title
- First/Last name
- Business unit
- Phone
- and many more.
- The login ID
- The password
- The password is never sent back in a web form. A hacker can not view source to see the details.
- The base access level for this user.
- Owner- Most access controls do not apply to the owner of the system "with great power comes great responsibility"
- User- Most user actions are controlled by a series of complex Access Control Limits
- Readonly - All the restrictions of a user but in addition all classes are readonly by default.
- Guest- Has no access by default, tables and records must be expressly granted.
- Disable the user.
- The user will no longer able to access the system.
- Any current session will be terminated.
- Force expire the user's password.
- The user will be required to change their password the next time they log in.
- "Force expire" is defaulted on when an administrator resets the user's password.
- Never expire is only used for functional accounts.
- This option should be used sparingly.
- A login that is marked as never expire will not be disabled even if multiple wrong password attempts are made.
- One primary account is often marked as "never expiry" so that you are not lock out of the system by a hacker attempting 5 times on all logins.
- Functional allows multiple concurrent users to use the same login.
- Normally the system logs out a user when they login with a different browser. This makes it very obvious if someone is using your account.
- SSO mode and Domain are used for integration with Microsoft NTLM single sign on and can only be used within an Microsoft intranet environment.
Password Storage Algorithms
| Type | Description |
| Best Practice 2017 |
A salted & PBKDF2 hash of the password with 23456 iterations. The resulting hash is stored in the database as an encrypted value. Key length 1024 Performance
Advantages:-
Risks:-
References:-
|
| Encrypted Salted PBKDF2 and SHA-512 Hashed 1234 times. |
A salted & PBKDF2 hash of the password with a large number (1234) of iterations. The resulting hash is stored in as encrypted value with a key length of 64 Performance
Advantages:-
Risks:-
References:- |
| Encrypted Salted SHA-512 Hash |
A salted and SHA-512 hash of the original password stored in as encrypted value. Advantages:-
Risks:-
|
| Salted Encrypted |
The password with a random salt is stored in an encrypted format in the database. The encryption key is stored in a separate database to the encrypted value. Risks
Advantages
|