January 18, 2021
Do you have a process to manage complaints?
stSoftware has a Complaints Handling Policy
Complaints Handling
stSoftware's complaints management policy is intended to ensure that we handle complaints fairly, efficiently and effectively.
We are committed to seeking and receiving feedback and complaints about our services, systems, practices, procedures, products and complaint handling.
Any concerns raised in feedback or complaints will be dealt with within a reasonable time frame.
People making complaints will be:
- provided with information about our complaint handling process
- provided with multiples and accessible ways to make complaints
- listened to, treated with respect by staff and actively involved in the complaint process where possible and appropriate, and
- provided with reasons for our decision/s and any options for redress or review.
stSoftware expects staff at all levels to be committed to fair, effective and efficient complaint handling and promotes a culture that values complaints and their effective resolution.
Our staff are empowered to resolve complaints promptly and with as little formality as possible. Where possible, complaints will be resolved at first contact with stSoftware.
Making a complaint
Complaints can be made anonymously or with details, through the below channels;
Email support@stsoftware.com.au
Ph 1300 78 73 78
Int +1 917 267 7607
Complaint management process
stSoftware's complaint management system ensures a consistent approach to our complaints management process.
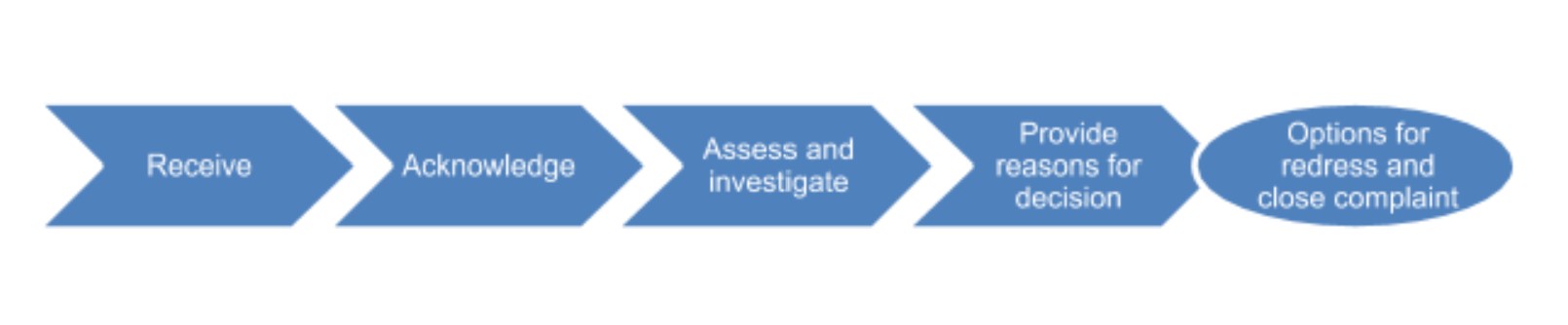
stSoftware is committed to improving the effectiveness and efficiency of our complaint management system. To this end, we analyse learnings and engage in continuous improvement.
Alternative avenues for dealing with complaints
When possible we will inform people who make complaints to or about us about any internal or external review options available to them (including any relevant Ombudsman or oversight bodies).